How to use proxies FULL TUTORIAL
Set a Proxy in Firefox
Open Firefox and click on the Tools menu and then click Options.
You should get a screen similar to the following:
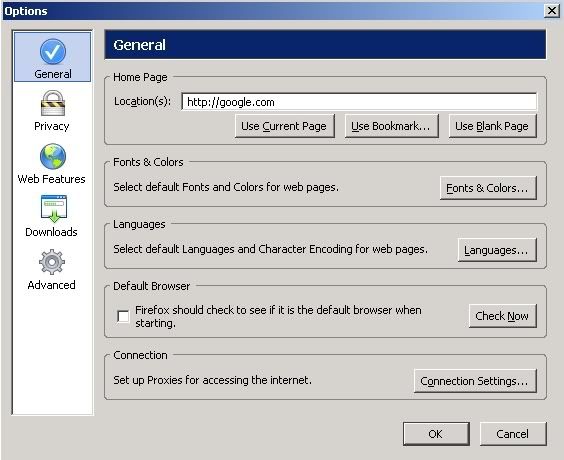
Click Connection Settings and the following should popup:
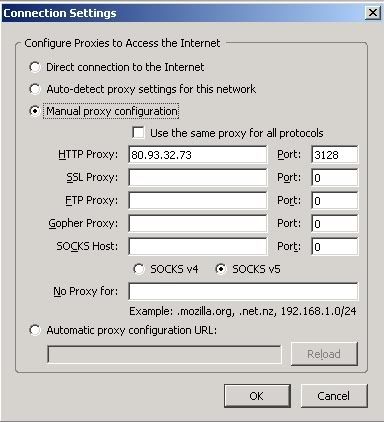
Select Manual Proxy Configuration and fill in the relevent field for your Proxy.
Note that Firefox's support for Authentication on Socks Proxy Servers is somewhat limited.
Types of Proxy Servers
There are many different types of Proxy Servers out there.
Depending on the purpose you can get Proxy Servers to route any of these common protocols, and many more:
FTP
HTTP
Gopher
IRC
MSN
AIM
ICQ
VOIP
SSL
So out of the common types of Proxy Servers, you end up with the following:
FTP Proxy Server:
Relays and caches FTP Traffic.
HTTP Proxy Server:
A one way request to retrieve Web Pages.
Socks Proxy Server:
A newer protocol to allow relaying of far more different types of data, whether TCP or UDP.
NAT Proxy Server:
This one works a little different, it allows the redirection of all packets without a Program having to support a Proxy Server.
SSL Proxy Server:
An extension was created to the HTTP Proxy Server which allows relaying of TCP data similar to a Socks Proxy Server.
This one done mainly to allow encryption of Web Page requests.
Furthermore, a Proxy Server can be split into another two Categories:
Anonymous:
An Anonymous Proxy Server blocks the remote Computer from knowing the identity of the Computer using the Proxy Server to make requests.
Transparent:
A Transparent Proxy Server tells the remote Computer the IP Address of your Computer. This provides no privacy.
Anonymous Proxy Servers can further be broken down into two more categories, Elite and Disguised.
An Elite Proxy Server is not identifiable to the remote computer as a Proxy in any way.
A Disguised Proxy Server gives the remote computer enough information to let it know that it is a Proxy,
however it still does not give away the IP of the Computer it is relaying information for.
What is a Proxy/Socks Chain
This is quite simple...
A Proxy Server Chain is when multiple Proxy Servers are linked together.
This is done for many reasons, from bypassing security restrictions, to providing extended Anonymity for connections.
Your computer connects to the first Proxy Server in the Chain, then requests that it connect to the second Proxy Server,
which then Connects to the third Proxy Server and so on.
At the end of the Chain, the last Proxy Server then makes a connection to the intended Host and data transmission starts.
This can only be done with Socks or SSL Proxy Servers.
It also can be quite unreliable.
also, you can use Proxifier.
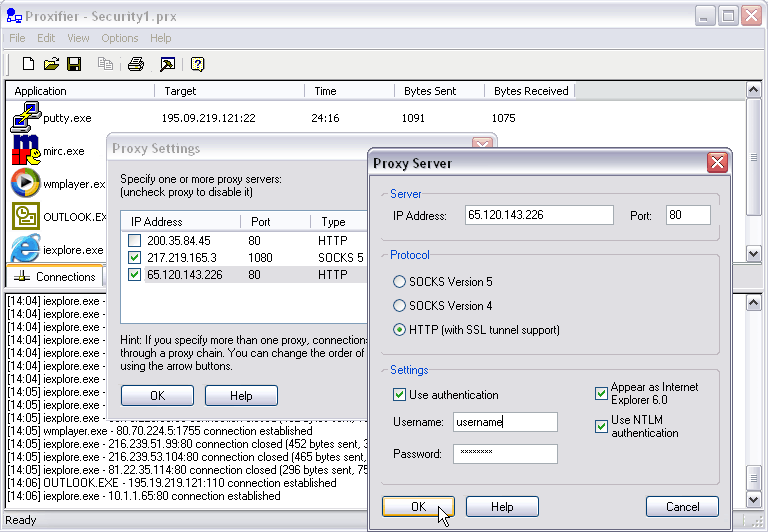
Code:
http://rapidshare.com/files/146497016/Pr....7.0.1.rar
Info:
Proxifier is a program that allows network applications that do not support working through proxy servers to operate through an HTTPS or SOCKS proxy or a chain of proxy servers.
With Proxifier you can easily tunnel all connections on the system or separate applications.
There are many network applications that do not support working through proxy servers and thus cannot be used behind a LAN or firewall(s). These can compromise corporate privacy and lead you to many other restrictions. Proxifier solves all of these problems and gives you the opportunity to work with your favorite software without any restrictions. Additionally, it lets you gain extra control over network security, create a proxy tunnel and add more power to network functionality.
Proxifier allows you to:
* Run any network applications through proxy server; no special
* configuration is required for the software.
* Access the Internet from restricted local area network through a proxy server gateway.
* Bypass firewall restrictions (connect to restricted ports).
* Use three types of proxy servers: SOCKS v4, SOCKS v5, and HTTP.
* "Tunnel" the entire system (force all network connections in the system work through a proxy server).
* Resolve DNS names through a proxy server.
* Use flexible Proxification Rules.
* Secure privacy by hiding your IP address.
* Work through a chain of proxy servers using different protocols.
* Use NTLM authentication on HTTP proxy
* View information on current connections (addresses, rate, data transfer, connection time, etc.) in real-time.
* View information on bandwidth usage as a colored diagram in real-time.
Maintain log files.
* Log incoming and outgoing traffic.
* Get detailed reports on network errors.
Open Firefox and click on the Tools menu and then click Options.
You should get a screen similar to the following:

Click Connection Settings and the following should popup:

Select Manual Proxy Configuration and fill in the relevent field for your Proxy.
Note that Firefox's support for Authentication on Socks Proxy Servers is somewhat limited.
Types of Proxy Servers
There are many different types of Proxy Servers out there.
Depending on the purpose you can get Proxy Servers to route any of these common protocols, and many more:
FTP
HTTP
Gopher
IRC
MSN
AIM
ICQ
VOIP
SSL
So out of the common types of Proxy Servers, you end up with the following:
FTP Proxy Server:
Relays and caches FTP Traffic.
HTTP Proxy Server:
A one way request to retrieve Web Pages.
Socks Proxy Server:
A newer protocol to allow relaying of far more different types of data, whether TCP or UDP.
NAT Proxy Server:
This one works a little different, it allows the redirection of all packets without a Program having to support a Proxy Server.
SSL Proxy Server:
An extension was created to the HTTP Proxy Server which allows relaying of TCP data similar to a Socks Proxy Server.
This one done mainly to allow encryption of Web Page requests.
Furthermore, a Proxy Server can be split into another two Categories:
Anonymous:
An Anonymous Proxy Server blocks the remote Computer from knowing the identity of the Computer using the Proxy Server to make requests.
Transparent:
A Transparent Proxy Server tells the remote Computer the IP Address of your Computer. This provides no privacy.
Anonymous Proxy Servers can further be broken down into two more categories, Elite and Disguised.
An Elite Proxy Server is not identifiable to the remote computer as a Proxy in any way.
A Disguised Proxy Server gives the remote computer enough information to let it know that it is a Proxy,
however it still does not give away the IP of the Computer it is relaying information for.
What is a Proxy/Socks Chain
This is quite simple...
A Proxy Server Chain is when multiple Proxy Servers are linked together.
This is done for many reasons, from bypassing security restrictions, to providing extended Anonymity for connections.
Your computer connects to the first Proxy Server in the Chain, then requests that it connect to the second Proxy Server,
which then Connects to the third Proxy Server and so on.
At the end of the Chain, the last Proxy Server then makes a connection to the intended Host and data transmission starts.
This can only be done with Socks or SSL Proxy Servers.
It also can be quite unreliable.
also, you can use Proxifier.
| This image has been resized. Click this bar to view the full image. The original image is sized 768x532. |

Code:
http://rapidshare.com/files/146497016/Pr....7.0.1.rar
Info:
Proxifier is a program that allows network applications that do not support working through proxy servers to operate through an HTTPS or SOCKS proxy or a chain of proxy servers.
With Proxifier you can easily tunnel all connections on the system or separate applications.
There are many network applications that do not support working through proxy servers and thus cannot be used behind a LAN or firewall(s). These can compromise corporate privacy and lead you to many other restrictions. Proxifier solves all of these problems and gives you the opportunity to work with your favorite software without any restrictions. Additionally, it lets you gain extra control over network security, create a proxy tunnel and add more power to network functionality.
Proxifier allows you to:
* Run any network applications through proxy server; no special
* configuration is required for the software.
* Access the Internet from restricted local area network through a proxy server gateway.
* Bypass firewall restrictions (connect to restricted ports).
* Use three types of proxy servers: SOCKS v4, SOCKS v5, and HTTP.
* "Tunnel" the entire system (force all network connections in the system work through a proxy server).
* Resolve DNS names through a proxy server.
* Use flexible Proxification Rules.
* Secure privacy by hiding your IP address.
* Work through a chain of proxy servers using different protocols.
* Use NTLM authentication on HTTP proxy
* View information on current connections (addresses, rate, data transfer, connection time, etc.) in real-time.
* View information on bandwidth usage as a colored diagram in real-time.
Maintain log files.
* Log incoming and outgoing traffic.
* Get detailed reports on network errors.
makasih gan infonya, selalu sajikan berita yg bermanfaat ya gan